After non-stop security problems with password manager LastPass, I decided to make my own: aeKee.com.
It’s an entirely browser based system and all encryption is performed client side in the user’s browser before being data is sent to the server for secure storage. Industry standard encryption techniques and algorithms are used throughout.
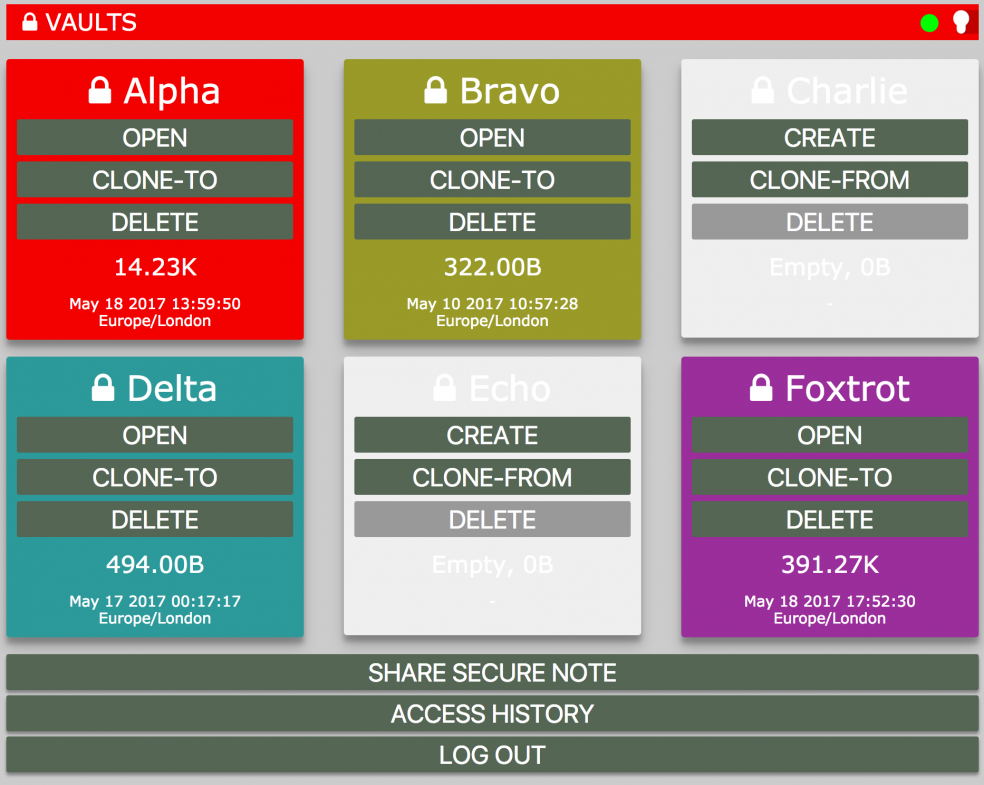
Main features are:
* Password manager. Stores all of your passwords and secure notes with easy rapid access so long as you’ve passed security.
* Password generator. Unique, strong, long, brute-force proof passwords are generated automatically as required.
* Secure note storage. Safely store secure plain-text information in your vault.
* Secure note sharing. Send an encrypted message to someone by email. If they know the password, they can decrypt it and see what it says.
From the FAQ…
How secure is it?
There are a number of pieces of information involved, and we secure them in different ways as follows:
login credentials
When you register and log in, your email address and account password are transmit (posted) to us over an SSL connection (the data portion of which is not logged) then salted and one-way hashed using the latest PHP7.1 password hashing algorithm and stored on our server in a caged file system using CloudLinux and CageFS. Even if someone gained access to the data we store, they would not be able to do anything with it – it has been one way hashed. Here’s an example data block for an account’s credentials:
ipbHk0P39W3D1iP2J1r6vdvFxY9olQN8is4eLlidb09PGtWx1ZLNvc1ed87756b1f75dcb91d549c531d52c216831da24b2e3e079244e9d374f04e2f20e4aac1790f8727934328231ba00bze919osbMqYOsgrGvd6XoqOO8P3D0KTC2gFYjhUOzD8nlyrMCGbPGtyWe do not store your email address or password in a reversible way.
Your email address and password are used to encrypt your 2fa (two factor authentication) secret (there’s an encrypted secret in the block of characters above) – this is done reversibly such that when you log in we can decrypt your 2fa secret in order to determine if the 2fa digits you enter correspond correctly with the ones Google Authenticator says they should.
Your vault(s)
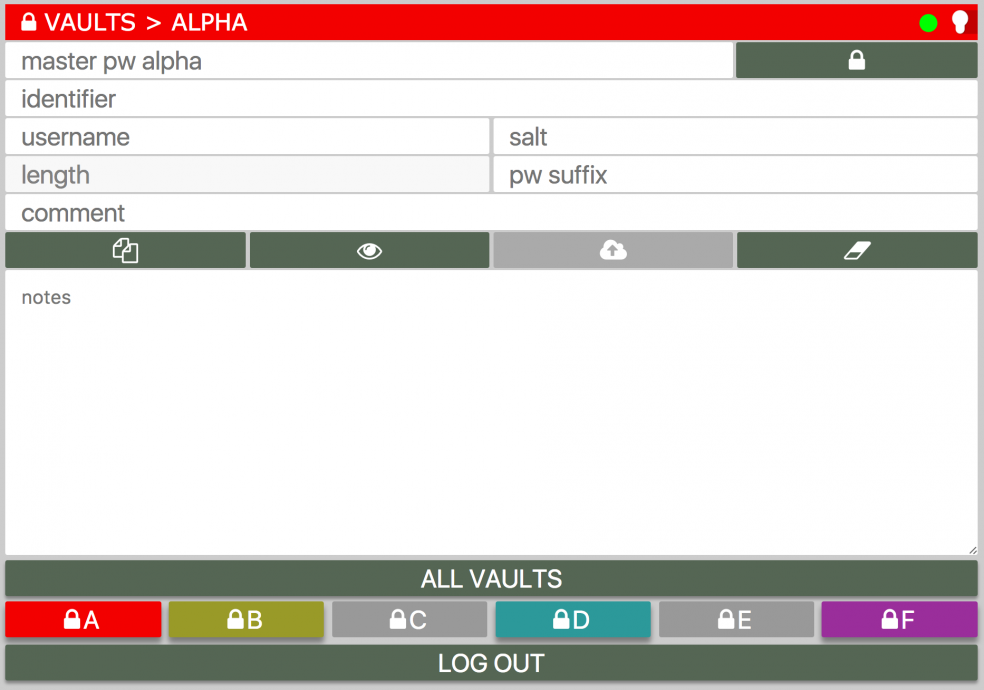
Your vault data is stored on our server encrypted. All encryption and decryption of your vault is done by JavaScript in your browser. Our server never sees your master vault password(s) encrypted, hashed or otherwise, at all. The encryption process starts with generating two keys from your master vault password, KeyE and KeyM, using PBKDF2 and a variable number of iterations around 9000 (which takes a large amout of computing power, confounding possible brute force attack attempts). A strong random initialisation vector, called an IV, is generated. The data is then padded using PKCS#7 to match the AES block size and encrypted using SHA256 in CBC mode using the IV and key KeyE. The result of this operation is then concatenated with the IV and hashed using the HMAC algorithm also using SHA256 but this time with KeyM. The concatenation of HMAC + EncryptedData + IV form your vault. The encryption process provides you with guaranteed confidentiality. The HMAC process provides you with guaranteed data integrity.
Here’s what’s stored on the server for a vault with very little in it:
Whd7rF6hzwgOQDz1TgcJtAr8LTyZSh1p0sXpxQDBnPoLTAp0uwBDHVciCKrqfAU9U6/tQTAQed0BLoLz4NEGLZtX97yBAN1xAaX6GnM3Q+QF2O9M1Jz90gTyQj4JNsAt1Rs7h0/1r61GtargElsPVID+kwnzoj4N3TJAAV+9omImoSWMFsfxSw2vR7dNTkXA=abeca7302a422620f744a452e8b769d43dd5f1f8d315dff38d3cbbc77e3826015Access Logs
A record of your logins and failed logins is kept however this data is encrypted on the server side using a salt and a PBKDF2’d version of your account login credentials. We do not know your login credentials and so we cannot decrypt these logs – only you can. Here’s an example record of a login event. It includes the remote IP address, the time, and browser details:
772e32a46e4504dcb13508e43b118900c7b3e7c4bef79419379f2cf34ffaf8a47d84fc05142bfe7923e3385268a0ac7f55c8ebbdf7b30633c655e28144abf87ef81f20ec2ef1adf0026c28c350d2bc248de8bc7ecb373e5ae7ccd737ecaa05e9f60c4ea80ea9b0e79ae525ab0e837efa84e67b71f17caedefe90f6b5e6186e98ade81d37f45975bc9398cd4f0a15e7e7472588133e5d3443e694b91cc93e272d0266c6479809a0d492b2b1e9f3edc216.Shared Notes
Notes are encrypted (in the same way vaults are) in the browser then uploaded and stored on our server when ‘sent’. The specified recipient receives an email with a link, and a plain-text comment from the sender. If the recipient knows the correct password, they are able to decrypt and view the message. The moment the recipient clicks on the link, the server copy of the message is destroyed so it can never be seen again.
Here’s an example – this example is unique in that, for the purposes of this demonstration, the server does not destroy its local copy.
The password is: aetherweb
Server Files
Our server is as secure as we can possibly make it. We work very very hard to achieve this and it would be foolhardy to go into public technical detail. Rest assured we’ve taken every normal measure, and a lot of additional ones too. Regardless, even the best servers get compromised from time to time so we’ve built this entire application with the insistance that should all data on our server be made public, there is no risk to our users’ confidentiality or integrity. Additionally, all of the application files on the server are scanned routinely (we use SHA3-512 hashes) and compared to the known release versions – any differences detected are immediately highlighted to us so that we can take instant remedial action.
![]()
![]()
![]()